Contact Centers, Chat, and Email: PII Detection in Customer Communications

Customer communication channels present unique PII detection challenges due to their interactive, real-time nature and the variety of sensitive information customers share. Building on the performance analysis in "The Specialization Gap: Purpose-Built vs. General Market PII Detection Solutions (Benchmark Results)," we can see how these challenges play out across different communication channels. Here's how different detection approaches perform across these critical business communications.
Contact Center and Call Transcripts
Detecting PII in call transcripts can be a challenging task due to various factors, such as transcription errors and difficulties related to active conversations with interruptions. These represent exactly the kind of real-world complexities that make traditional regex-based approaches inadequate, as explained in "The Hidden PII Detection Crisis." Conversations often involve multiple speakers, interruptions, language changing (code-switching) and incomplete sentences, which can obscure context and split PII entities into pieces, making it challenging to identify and redact sensitive information accurately.
Moreover, transcription errors can result in false positives or false negatives, which can compromise the accuracy of PII detection. Therefore, it is essential to use AI-based PII detection specifically meant to mitigate these challenges and provide reliable and accurate protection against data breaches and other security threats.
The Transcription Challenge
For example, ASR tools commonly transcribe numerical strings, such as a credit card number, as a combination of characters and digits: "one two three 4 5 six 7". This kind of variation stumps regex-based or checksum approaches like Luhn. Another common issue is partial credit card numbers.
Consider this comparison:

Call Transcript Performance Results1
Using the evaluation methodology detailed in "How to Properly Benchmark PII Detection Solutions," here are the call transcript results:

Chat Logs: The B2B Challenge
Chat logs are another common interaction source where a large amount of sensitive data are exchanged. In a B2B scenario, the purpose of a chat is often for account verifications, updating payment details, or otherwise updating or requesting information that is privileged to the user making the request. While this information is indeed needed during the actual conversation, once the conversation is complete, storing this information poses problems of potential data loss and compliance issues.
For example, if a user chooses to update their credit card information in a chat, that information should be immediately deleted afterwards. Furthermore, many users will give information in a chat that is not strictly necessary in the transaction, including sensitive medical history. The best way to deal with these problems is to employ a redaction technology that omits any potentially sensitive information before landing in your data center.
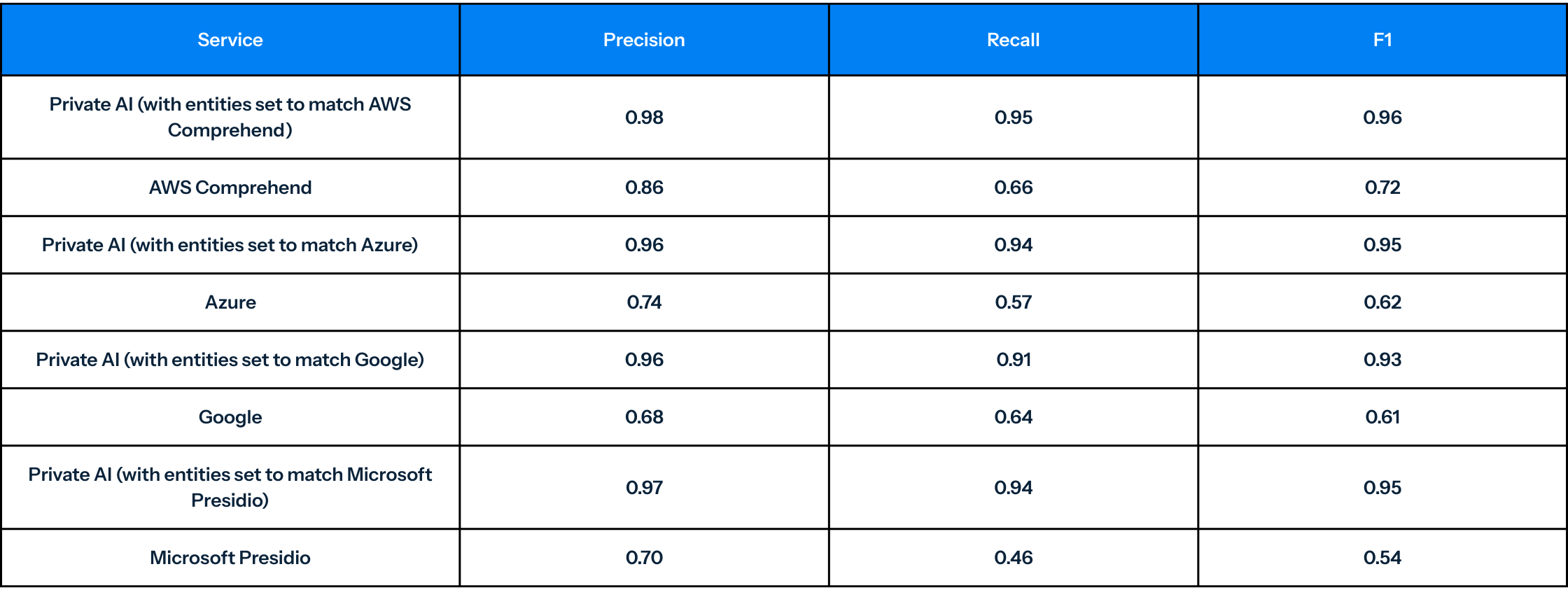
Chat Log Performance Results1
Email: The Document-Rich Environment
Similar to chat logs, emails contain a wealth of private and sensitive information that is, at the bare minimum, confidential to the company that is sending or receiving the information and, at worst, might contain:
Personal Identifiable Information (PII): This could include social security numbers, driver's license numbers, personal addresses, and phone numbers.
Financial Information (PCI): This could include bank account numbers, credit card numbers, income details, credit history, or company financial records and forecasts.
Confidential Company Data (CCI): This might be strategic plans, non-public financial trends, new product information, or other proprietary information that a company wouldn't want its competitors to know.
Information within documents commonly found in email, such as:
- Legal Documents: These might include contracts, litigation histories, or other sensitive legal information.
- Health Records (PHI): These include patient health information, medical histories, and insurance claim data. The complexity of detecting PHI in email attachments mirrors the challenges discussed in "Healthcare and Medical Data: The Ultimate PII Detection Challenge."
- Documents containing Intellectual Property: These could be patents, copyrights, trademarks, or trade secrets that are valuable assets to a company and its competitive edge.
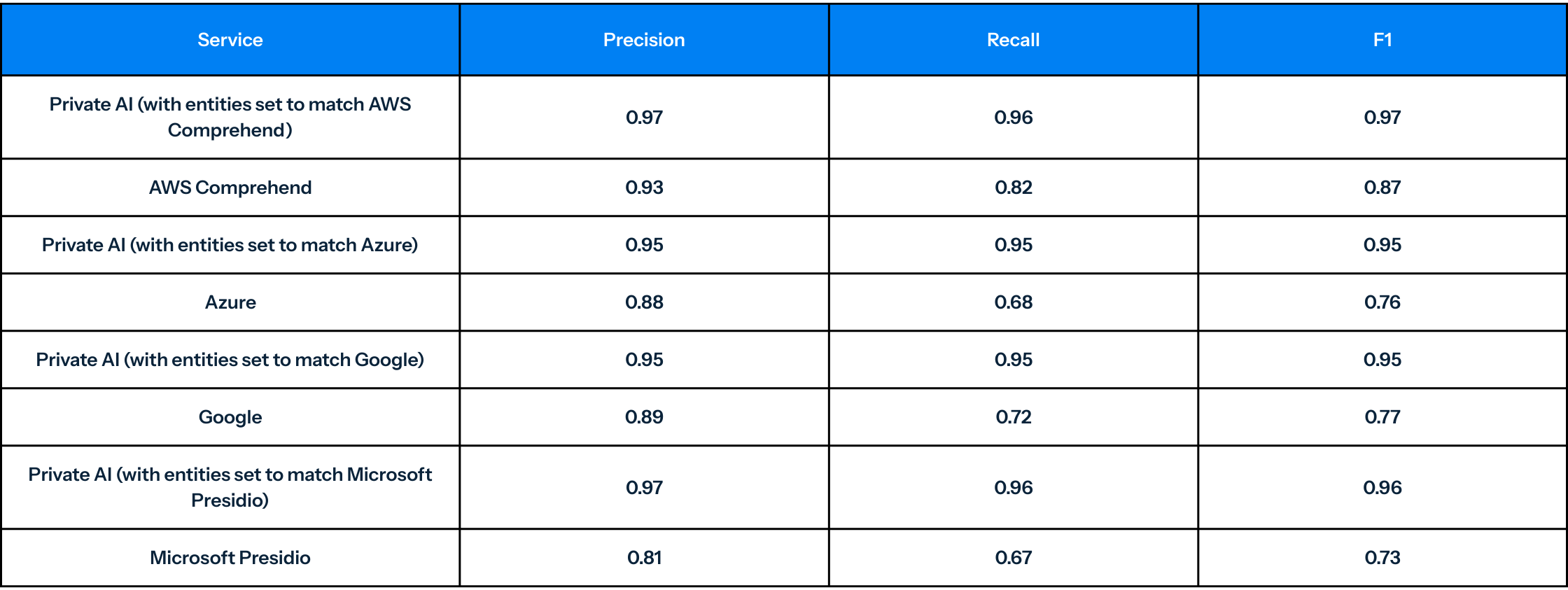
Email Performance Results1
The Business Impact
For businesses handling customer data, performance differences translate directly into compliance risk, potential data breaches, and customer trust issues. When customers share sensitive information through your communication channels, they trust you to protect it. Missing 18-32% of that sensitive data is not just a technical failure, it's a breach of customer trust.
These customer communication challenges, combined with the medical data complexities covered in "Healthcare and Medical Data: The Ultimate PII Detection Challenge," demonstrate why organizations need a comprehensive purpose-built AI-based approaches to privacy protection.
1 Last compared October 2024





































































































