Data security and integrity are two critical concepts in the world of cybersecurity. While they are often discussed together, they have distinct definitions and implications. Data security encompasses the processes and technical safeguards established to preserve data integrity, as well as confidentiality and availability of data. In this article, we will dive into the details of what data integrity and data security entail, how they are related, and the importance of protecting against data integrity attacks. Additionally, we will discuss the recent draft update of the NIST Cybersecurity Framework (CSF) 2.0, a comprehensive tool that reflects the evolving cybersecurity landscape and offers valuable guidance for ensuring data integrity and security across all organizations.
Data Integrity
Data integrity is defined by the Committee on National Security Systems as “the property that data has not been changed, destroyed, or lost in an unauthorized or accidental manner.” In other words, it refers to the accuracy, completeness, and consistency of data throughout its lifecycle. To maintain data integrity, then, an organization must ensure that data remains unchanged, and any modifications to data are authorized, recorded, and properly tracked. Data integrity is essential for data quality, as it helps to ensure that data is reliable, trustworthy, and can be used for sound decision-making.
Data Security
In order to protect an organization from a data integrity loss event, the data must be properly secured. Data security refers to the measures taken to protect data from unauthorized access, use, disclosure, modification, or destruction. Data security involves a range of practices and technologies that, at each stage of the life cycle of the data, from collection until its destruction, prevent unauthorized access to data, such as encryption, access controls, firewalls, and intrusion detection systems. Data security cares about more than protecting the data’s integrity; it must also ensure its confidentiality and availability.
NIST Cybersecurity Framework 2.0
NIST has recently overhauled its Cybersecurity Framework (CFS), first released almost a decade ago, and published a draft for public commentary. The 2.0 version reflects a number of major changes to the NIST CSF Version 1.1. For example, it expands the framework’s scope from protecting critical infrastructure to providing cybersecurity for all organizations regardless of type or size. Also, a new “govern” function has been added to emphasize that cybersecurity is a major source of enterprise risk, ranking alongside legal, financial, and other risks as considerations for senior leadership. The new function outlines the process by which an organization formulates and implements internal decisions to bolster its cybersecurity approach. We can expect enhanced guidance and sector-specific examples of implementation measures aiding with the management of cybersecurity risks.
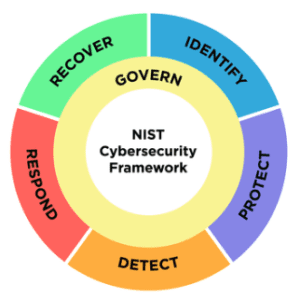
Source: DRAFT NIST Cybersecurity Framework 2.0
Protecting Against Data Integrity Attacks
Many different attacks to systems and data are possible and the NIST Framework applies to them broadly. But applied specifically to a data integrity attack, three phases can be distinguished: (1) identify assets and implement protections, (2) discover data integrity incidents, and (3) recover from the incident.
An example of an action that must be taken in phase one is limiting access and permissions to an organization’s data to only those roles within the business that require access in order to perform their functions, which is an effective way to minimize the potential for accidental modification of data. The fewer people that are permitted to alter the data, the less likely that is to happen.
Phase two requires sophisticated tools to detect an occurring attack. By continuously comparing what has been determined as the ”normal state” with the status quo, any deviations can be surfaced and assessed to identify an attack. This phase is not particular to integrity attacks only.
A key data security measure that is geared towards recovering from a data integrity attack is having in place reliable backup systems. In case an unauthorized change, destruction, or loss of data has occurred, the data can be restored to its uncompromised form from the backup. These backup systems should enable recovery from sufficiently long ago to allow restoring data in instances where the data has been corrupted without being detected for a while. Some ransomware attacks start months before security experts become aware of them, by which time their recent backups might all be corrupt.
Conclusion
Data integrity cannot be achieved without data security, but the latter protects against broader attacks than just unauthorized change, destruction, and loss. In particular, the confidentiality and availability of data are likewise under the umbrella of data security. Private AI is first and foremost geared towards protecting personal information, which is an aspect of the broader mandate of data security, which protects all data and needs to understand the types of information that needs protecting. Personal information is a particularly sensitive corporate asset and privacy legislation requires data security measures to be implemented for its protection. One measure that Private AI is a global leader in is the redaction of personal data in unstructured data. If all else fails, it is most comforting to know that an intruder will not be able to reap any benefits from the data they gained access to because it is de-identified. To see the tech in action, try our web demo, or sign up for an API key to try it yourself on your own data.



